The Cybersecurity Practice Imperative
by Ramesh Chitor, Satya Dillikar, Kush Bhardwaj, Kayshav Bhardwaj and Maya Chitor.
1. Abstract
Cybersecurity in its broadest definition encompasses a wide range of practices, technologies, standards, tools, and concepts related closely to those of information and operational technology (OT) security. Cybersecurity protects against adversarial attacks and should never be used for offensive/nefarious purposes. One thing distinctive about cybersecurity is it is the only ‘science’ or tech field with a human adversary.
In recent times, with the explosive and sophisticated growth of ransomware attacks, institutions, practitioners, and end-users arestruggling to put better proactive data security practices in place. Organizations are constantly in search of advanced practices to keep the bad actors out of data access., Data Management, Data Governance, Compliance, Mobility, and Data Security platforms add new dimensions to this burning issue.
Cybersecurity constraints should be introduced early during software development as part of secure development methodologies and practices. In April 2023, CISA and its partners issued secure-by-design principles for software manufacturers. This paper provides a primer for an audience with little to no prior knowledge of Cybersecurity essentials. Relevant use cases for compliance and audit methods are highlighted while outlining requirements for strong Cybersecurity practices that encompass software, hardware, and relevant services are recommended.
This paper describes the elements of a CyberSecurity Practice and outlines key methodologies. All levels of audience are welcome to digest the contents of this document.
2. Cybersecurity History
In this year itself, Cybercriminals delivered a wave of cyberattacks that were not just highly coordinated, but far more advanced than ever before seen. Ransomware attacks hit small businesses and huge corporations alike. It was a year of massive data leaks, expensive ransomware payouts, and a very complicated and sophisticated threat landscape.
Cybersecurity attacks vary in severity and sophistication. Some of them include highly-coordinated, multi-step attacks
- Usage of old technology to launch new cyberattacks
- Use of fake logins, sign-up sites, and stolen identities to gain access to critical data
Ransomware attacks: Ransomware is a type of malware that prevents or limits users from accessing their system, either by locking the system’s screen or by locking the users’ files until a ransom is paid. Modern ransomware families, collectively categorized as crypto-ransomware, encrypt certain file types on infected systems and force users to pay the ransom through certain online payment methods to get a decryption key.
The very first inference of a ransomware attack: Even though ransomware has been in the headlines consistently over recent years, the idea of taking user files or computers hostage by encrypting files, hindering system access or other methods – and then demanding a ransom to return them has been around. In the late 1980s, criminals were already holding encrypted files hostage in exchange for cash sent via the postal service. One of the first ransomware attacks ever documented was the AIDS trojan (PC Cyborg Virus) that was released via floppy disk in 1989. Victims needed to send $189 to a P.O. box in Panama to restore access to their systems, even though it was a simple virus that utilized symmetric cryptography.
With the emergence of cryptocurrencies, the frequency of ransomware attacks has gone up drastically. In 2013, a new type of ransomware that encrypted files aside from locking a system emerged. The encrypted files ensured that victims were forced to still pay the ransom even if the malware itself was deleted. Due to this novel behavior, it was dubbed “CryptoLocker”. Like previous ransomware types, crypto-ransomware demands payment from affected users in exchange, this time, for a decryption key to unlock the encrypted files.
When George Kurtz, CEO of Crowstrike testified in front of the Select Senate Committee on Cybersecurity and Supply Chain Threats, he said that it was abundantly clear that organizations were consistently failing to adequately defend themselves.
3. Cybersecurity Architecture
The dimensions of a cybersecurity architecture are:
Figure-1: Cybersecurity Dimensions
- Technical dimension: This dimension includes the selection, configuration, and implementation of technical solutions to protect the organization’s assets, such as networks, devices, applications, and data. This includes technologies such as firewalls, intrusion detection and prevention systems, antivirus software, encryption, and access control systems.
- Operational dimension: This dimension includes the development and implementation of policies, procedures, and processes to manage cybersecurity risks and incidents. This includes activities such as risk assessment, vulnerability management, security awareness training, incident response planning, and security monitoring.
- Physical dimension: This dimension includes the protection of physical assets, such as buildings, equipment, and storage facilities. This includes physical security measures such as access control, surveillance, and environmental controls.
- Human dimension: This dimension includes the role of people in cybersecurity architecture. This includes training and awareness programs for employees, contractors, and partners to promote good security practices, as well as policies and procedures to manage insider threats and social engineering attacks.
- Legal and regulatory dimension: This dimension includes compliance with relevant laws, regulations, and industry standards. This includes activities such as data privacy and protection, data breach notification, and compliance with regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
All of these dimensions must be considered when designing and implementing a cybersecurity architecture to ensure that the organization’s assets are protected against cyber threats and risks. A comprehensive and integrated approach to cybersecurity is essential to ensure the confidentiality, integrity, and availability of the organization’s data and systems.
The elements of a cybersecurity architecture include:
- Network security: This involves the use of firewalls, intrusion detection/prevention systems, and other technologies to protect the organization’s network and systems from external threats.
- Endpoint security: This involves the use of antivirus software, encryption, and other technologies to protect the organization’s endpoints (such as laptops, desktops, and mobile devices) from malware, unauthorized access, and other threats.
- Data security: This involves the use of technologies such as encryption, data loss prevention, and data backup and recovery systems to protect the organization’s data from unauthorized access, loss, or theft. This includes both data-at-rest and data-in-transit.
- Application security: This involves Secure coding practices, Vulnerability scanning and testing, Threat modeling, Authentication and authorization, and Secure deployment and configuration.
- Identity security: This involves the use of technologies such as multi-factor authentication, access controls, role-based access control, and identity and access management (IAM) systems to control access to the organization’s data and systems.
Figure-2: Cybersecurity Elements

- Infrastructure security: Infrastructure security refers to the measures and practices used to secure the underlying physical and virtual infrastructure of an organization, including hardware, software, and networks, from cyber threats and risks.
- Incident response: This involves the development of procedures and processes to respond to cybersecurity incidents in a timely and effective manner, including containment, eradication, and recovery. Effective incident response is critical to minimizing the impact of security incidents and mitigating potential harm to an organization’s assets and reputation.
- Security monitoring and analytics: This involves the use of tools and techniques such as security information and event management (SIEM) systems, threat intelligence, and user behavior analytics to detect and respond to security threats.
- Compliance and risk management: This involves the development of policies, procedures, and controls to ensure compliance with relevant laws, regulations, and industry standards, as well as the identification and management of cybersecurity risks.
- Cloud Security: Cloud security refers to the measures and practices used to secure cloud-based services and data from cyber threats and risks. This involves all of the above elements
All of these elements must be integrated into a comprehensive cybersecurity architecture to ensure the confidentiality, integrity, and availability of the organization’s data and systems, and to protect against cyber threats.
The cybersecurity landscape refers to the overall environment and conditions related to cybersecurity. It encompasses various aspects including all the dimensions and elements mentioned above. Here’s a breakdown of each component with each cybersecurity element number for illustration.
Figure-3: Cybersecurity Landscape – 1/2

Figure-4: Cybersecurity Landscape – 2/2
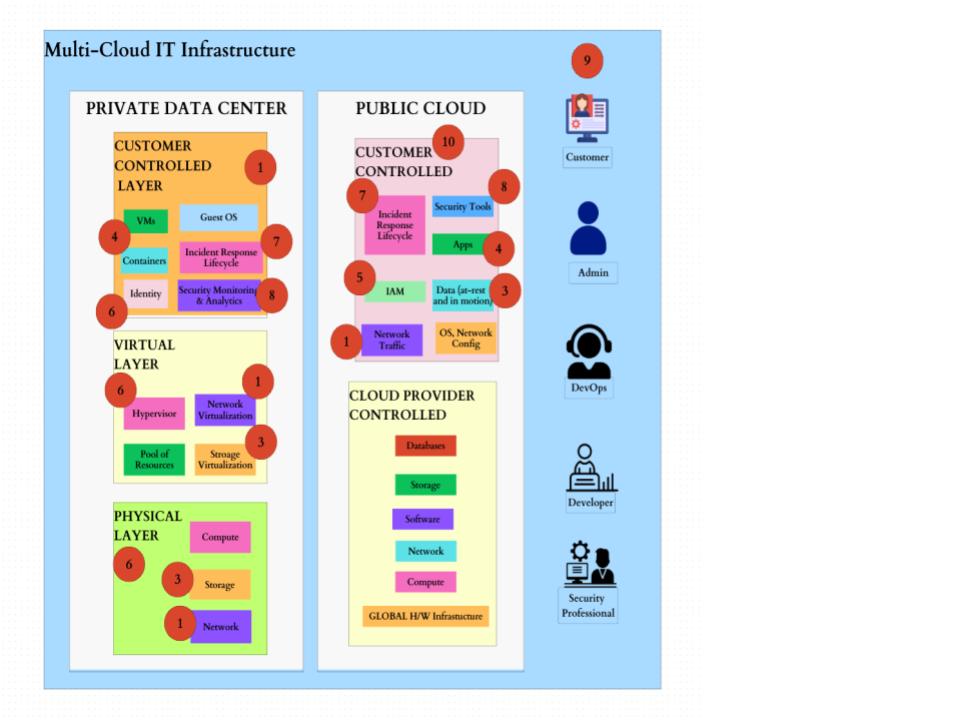
Legend: 1 – Network Security, 2 – Endpoint Security, 3 – Data Security, 4 – Application Security, 5 – Identity Security, 6 – Infrastructure Security, 7 – Incident response, 8 – Security Monitoring, 9 – Security Compliance, 10 – Cloud Security
4. Existing Standards and Bodies
Here are a few top existing standards, bodies, and architectures in the field of cybersecurity:
- ISO/IEC 27001: This is an international standard for information security management systems (ISMS). It provides a framework for organizations to establish, implement, maintain, and continually improve their information security practices.
- NIST Cybersecurity Framework (CSF): Developed by the National Institute of Standards and Technology (NIST) in the United States, the CSF is a risk-based approach to managing cybersecurity. It offers guidelines and best practices for organizations to assess and improve their ability to prevent, detect, and respond to cyber threats.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS is a set of security standards developed by the Payment Card Industry Security Standards Council (PCI SSC). It aims to ensure the secure handling of credit card information by organizations that process, store, or transmit cardholder data.
- Open Web Application Security Project (OWASP): OWASP is a non-profit organization dedicated to improving the security of software. It provides resources, tools, and guidelines for developers to build secure web applications and helps organizations understand and mitigate web application vulnerabilities.
- Common Vulnerabilities and Exposures (CVE): CVE is a list of publicly known cybersecurity vulnerabilities and exposures. It is maintained by the MITRE Corporation and serves as a common language for identifying and discussing vulnerabilities across different organizations and security tools.
- Security Operation Center (SOC): A SOC is an organizational unit responsible for monitoring, detecting, analyzing, and responding to cybersecurity incidents. It typically follows established processes and uses various technologies to provide round-the-clock monitoring and protection of an organization’s systems and data.
- Zero Trust Architecture (ZTA): Zero Trust is an architectural approach that assumes no trust by default, both inside and outside an organization’s network perimeter. It emphasizes strict access controls, continuous authentication, and detailed visibility to mitigate the risk of lateral movement and unauthorized access.
- Cloud Security Alliance (CSA): The CSA is a non-profit organization that promotes best practices and security assurance in cloud computing. They provide guidance and research on various cloud security topics, including governance, risk management, and compliance.
These are just a few examples, as the field of cybersecurity is vast and constantly evolving. Many more standards, bodies, and architectures play crucial roles in ensuring the security of information and systems.
5. Concept of a Cybersecurity Practice
The concept of good cybersecurity practices involves the steps and processes people take to keep themselves and the digital world safe and secure. It consists of a toolbox and plans to keep computer systems, networks, and information protected from unauthorized and unwarranted access and potential attacks from malicious parties. One primary component of safe cybersecurity practices is “risk assessment”. This would be an investigation that identifies potential vulnerabilities and threats that could pose harm to their systems. Another key element of proper cybersecurity practices is using strong and secure passwords or other methods of identification. By using unique and complex passwords, and techniques such as two-factor authentication, we can further prevent unauthorized access and protect our accounts. Additionally, a vital role in safe cybersecurity practices is to be educated and aware of ever-evolving threats and vulnerabilities. We must stay informed about the newest practices we can adopt to protect against the latest threats. Learning about how cyberattacks happen and techniques most commonly used by malicious attackers and how to mitigate those threats is a key way to staying safe. Updating software and operating systems can also keep your system up to date to protect itself in the event of an attack. These updates often contain patches and fixes for detected vulnerabilities.
6. Common Pitfalls of Legacy Architectures
Some common pitfalls of existing cybersecurity architectures:
- Reactive instead of proactive approach: Many existing cybersecurity architectures are designed to respond to known threats rather than proactively identifying and mitigating potential vulnerabilities. This reactive approach can result in delays in responding to new threats and can leave organizations vulnerable to attacks.
- Insufficient risk assessment and management: Some cybersecurity architectures may not have a comprehensive and continuous risk management process in place, leading to inadequate identification, assessment, and mitigation of cyber risks. This can result in an insufficient investment of resources in areas of highest risk.
- Lack of integration: Cybersecurity architectures that are not fully integrated may lead to gaps in security coverage and blind spots that can be exploited by cyber attackers. This can result in ineffective security measures, and ultimately, breaches.
- Overreliance on technology: Cybersecurity architectures that rely too heavily on technology solutions, such as firewalls and intrusion detection systems, may neglect other critical aspects of cybersecurity, such as employee training and awareness, and can leave organizations vulnerable to attacks.
- Insufficient incident response planning: Even the best cybersecurity architecture can be breached. Organizations need to have a plan for responding to incidents to minimize the damage. Some cybersecurity architectures may not have a comprehensive and tested incident response plan in place, leading to slow response times, confusion, and inadequate mitigation of security incidents.
- Failure to account for human factors: Cyber threats are not just technical. They also exploit human vulnerabilities. Cybersecurity architectures may not adequately address human factors, such as employee training and awareness, insider threats, social engineering attacks, and phishing attacks, which are often major sources of cybersecurity vulnerabilities.
- Inadequate investment in cybersecurity: Organizations may not be investing enough resources in cybersecurity, resulting in inadequate protection against cyber threats and risks. Cybersecurity is an investment, not an expense.
- Lack of awareness and training: Employees who are not aware of the cybersecurity risks they face or who are not trained on how to protect themselves and the organization’s data are a major vulnerability.
- Outdated technology: Organizations that use outdated technology are more vulnerable to attack. The cyber threat landscape is constantly evolving. Organizations need to make sure that their cybersecurity architecture is up-to-date and can protect against the latest threats.
- Poor security practices: Organizations that have poor security practices, such as weak passwords or a lack of access control, are more likely to be breached.
- Lack of governance: Organizations that lack strong governance over their cybersecurity program are more likely to have gaps in their security posture.
- Not having a holistic approach: Cybersecurity is not just about technology. It also involves people, processes, and culture. Organizations need to have a holistic approach to cybersecurity that considers all of these factors.
- Areas & Institutes of Research
- CyLab is the security and privacy institute at Carnegie Mellon University. Founded in 2003, they conduct cutting-edge research and collaborate with industry experts on privacy and security. They have developed new methods for preventing cyberattacks, and spread education on these topics to make a world where technology can be trusted.
- DARPA is the research and development sector of the United States Department of Defense. They conduct research, much of it classified, in cybersecurity and how to detect and thwart cyberattacks. They also create new encryption methods and state-of-the-art techniques for detecting and preventing breaches.
- MITRE is a nonprofit organization that conducts research in many technological fields, including cybersecurity. They develop tools, resources, and software, including the MITRE ATT&CK framework, to help defend against cyberattacks.
- The Cybersecurity and Infrastructure Security Agency (CISA) is a United States federal agency under the Department of Homeland Security that is responsible for protecting US infrastructure cyber threats. It works with federal agencies, state and local governments, and private sector organizations to advance cybersecurity and prevent malicious attacks.
7. Best Practices & Methodologies
Here are some best practices to secure a digital environment in an ever-evolving threat landscape:
- Implement Strong Access Controls: Use strong authentication methods like multi-factor authentication (MFA) to ensure that only authorized individuals can access sensitive systems and data. Regularly review and update user access privileges to maintain the principle of least privilege.
- Regularly Update and Patch Systems: Keep all software and systems up to date with the latest security patches. Vulnerabilities in outdated software can be exploited by attackers, so staying current is crucial.
- Conduct Regular Security Assessments: Perform periodic security assessments, including vulnerability scanning and penetration testing, to identify weaknesses in your systems. Address any discovered vulnerabilities promptly.
- Educate and Train Employees: Provide comprehensive cybersecurity awareness training to all employees. Teach them about common threats, social engineering techniques, and safe computing practices to minimize the risk of human error leading to security incidents.
- Implement Defense-in-Depth: Employ multiple layers of security controls to create a layered defense strategy. Combine technologies, policies, and procedures to provide overlapping security measures and increase the difficulty for attackers to compromise your systems.
- Implement Network Segmentation: Segment your network into smaller, isolated subnetworks to restrict the lateral movement of attackers. This can limit the impact of a potential breach and prevent unauthorized access to critical assets.
- Backup and Disaster Recovery: Regularly back up critical data and systems, storing backups securely and testing the restoration process. Having a robust disaster recovery plan helps minimize downtime and ensures business continuity in the event of a cyber incident.
- Follow the Principle of Least Privilege (PoLP): Grant users the minimum level of access necessary to perform their tasks. This minimizes the potential impact of compromised accounts and reduces the attack surface within your environment.
- Continuous Monitoring and Threat Intelligence: Implement a robust security monitoring system that collects and analyzes logs, network traffic, and system behavior. Combine this with threat intelligence feeds to detect and respond to emerging threats in real-time.
- Engage in Security Awareness and Training Programs: Provide regular cybersecurity awareness and training programs for all employees. Educate them about current threats, social engineering techniques, and safe computing practices to build a security-conscious culture.
- Establish an Incident Response Plan: Develop a comprehensive incident response plan that outlines roles, responsibilities, and procedures to follow in the event of a security incident. Regularly test and update the plan to ensure an effective response when needed.
Implementing the above-suggested best practices and methodologies can come with several challenges. Here are some common challenges encountered during implementation:
Resource Constraints: Organizations often face limited budgets, staffing, and time constraints, making it challenging to allocate adequate resources to implement and maintain robust security measures.
Complexity and Integration: Implementing multiple layers of security controls and technologies can result in complexity, especially when integrating different systems and tools. Compatibility issues and the need for seamless integration can pose challenges during implementation.
Balancing Security and Usability: Striking the right balance between implementing robust security measures and maintaining usability for employees and customers can be a challenge. Overly stringent security controls can hinder productivity and user experience.
Resistance to Change: Implementing new security practices often requires changes in workflows and user behavior. Resistance to change from employees and stakeholders can impede successful implementation.
Evolving Threat Landscape: The cybersecurity landscape is constantly evolving, with new threats and attack techniques emerging regularly. Keeping up with these evolving threats and promptly adapting security measures can be challenging.
Compliance and Regulatory Requirements: Meeting compliance standards and regulatory requirements, such as GDPR or HIPAA, can present challenges. Organizations need to ensure that their security practices align with the specific regulations applicable to their industry.
Lack of Standardization: The absence of universal standards and guidelines for implementing security best practices can make it challenging to navigate the wide array of frameworks, methodologies, and solutions available.
Conclusion
It comes as little surprise that decision-makers include cybersecurity among their top considerations when it comes to digital transformation. Worldwide spending on information security products and services exceeded $114 billion in 2018, and according to Gartner that market will $170.4 billion in 2023. According to an updated forecast from the International Data Corporation (IDC) Worldwide Semiannual Security Spending Guide, worldwide spending on securityrelated hardware, software, and services will rise 15.7% in 2024 to $106.6 billion and will continue growing, reaching $151.2 billion in 2025. As professionals, entities, organizations and as a community we need to collectively take Cyberthreats seriously and lead with zero trust in all scenarios. Furthermore, as the threat landscape evolves to focus on Identity Security and Identity Threat Detection and Response (ITDR), the need to raise awareness, train and communicate best best practices is of paramount importance.
Acknowledgement & References
1. Cost of a Data Breach Report 2022
https://www.ibm.com/downloads/cas/3R8N1DZJ
2.Gartner Identifies the Top Cybersecurity Trends for 2023
Gartner Identifies the Top Cybersecurity Trends for 2023
3. CyLAB
https://en.wikipedia.org/wiki/Carnegie_Mellon_CyLab
4. Cybersecurity Moonshot
http://web.mit.edu/ha22286/www/papers/IEEESP21_2.pdf
5. CISA https://fedscoop.com/cisa-and-partners-issue-secure-by-design-principles-for-software-manufacturers/
6. Crowdstrike CEO George Kurtz testifies https://www.intelligence.senate.gov/sites/default/files/documents/os-gkurtz-022321.pdf
7. Cybersecurity Tools https://www.techrepublic.com/article/even-with-cybersecurity-tools-deployed/amp/
8. The MITRE corporation
9. The Defense Advanced Research Projects Agency (DARPA)
……………………………
About the authors

Ramesh Chitor leads Go-To-Market efforts in the Cybersecurity space focussed on Identity, Threat Detection, and Response. Ramesh is a 20+ veteran in the IT industry with experience working on large revenue-impacting transformational projects at IBM, Cisco, Western Digital, Rubrik, and now at QOMPLX. You can reach Ramesh at ramesh.chitor@qomplx.com

Satya Dillikar is an experienced Cloud Software and Networking Architect and Practitioner with expertise in designing and implementing scalable secure cloud solutions. He is skilled in Public Clouds(AWS, Azure, and GCP) and excels in building resilient architectures and deploying cloud-native applications. He has contributed to many flagship products & SaaS services at companies like VMware, Cisco, Ciena, and Broadcom. With a strong commitment to safeguarding organizations, Satya is dedicated to maintaining a secure digital environment in an ever-evolving threat landscape. You can reach Satya at satya@softbuild.dev
Kush Bhardwaj is an aspiring scholar with interests in cybersecurity, and distributed computing. You can reach Kush at kush@kushbhardwaj.com
Kayshav Bhardwaj is a rising senior in high school whose interests lie primarily in artificial intelligence and data science. You can reach Kayshav at kayshav@kayshavbhardwaj.com
Maya Chitor is an incoming researcher at the Aspiring Scholars Directed Research Program with a focus on biotechnology. She is an 8th grader at BASIS Independent Fremont, CA. Maya can be reached by email at maya.chitor@gmail.com
